Permissions Required to Join Azure Files Share to Domain (Active Directory)
This article explains the permissions required for a non-administrator, delegated domain user service account used to join an Azure Files share to an Active Directory domain. If these permissions are not correct, you receive an error during the domain join step. Errors may include, but not limited to, "Access is denied" or "A required privilege is not held by the client."
This does not apply to Entra Domain Services environments. Entra Domain Services environments only need the feature enabled and they do not need to join the domain as a specialty service account. In Nerdio Manager, be sure to select Entra Domain Services in the Join to AD drop-down list.
Note: For ease of deployment, you can use a domain administrator or temporarily elevate the delegated service account to domain administrator rights.
A domain administrator account is sufficient to join the Azure Files share to your domain. However if you are using a service account and delegating specific permissions to that account, the "Add/Remove computer accounts" delegated permissions used for AVD session hosts are not sufficient to add Azure Files shares.
Additional Notes:
-
The domain join process for Azure Files must be executed in the context of a domain user. Nerdio Manager completes this process using the domain administrator credentials provided, or user credentials that have been delegated sufficient privileges following the steps detailed below. If you are not using domain administrator credentials, or if the domain administrator user does not receive local administrator privileges, Nerdio Manager's automation may not be able to complete the domain join.
-
In order for Nerdio Manager to execute these commands as the specified user, a command to change the user context is required. In order for this to be successful, the specified user credentials must also be granted local administrator privileges on the temporary VM provisioned by Nerdio Manager to complete this process. If the specified user does not have local administrative privileges, you may receive an error message indicating “Connecting to remote server azfilestmp-* failed with the following error message : Access is denied.” Please ensure the user account specified is granted local administrator permissions (for the azfilestmp-* VM only).
-
Domain administrative (or delegated) privileges are a requirement for the Azure Files domain join module, Local administrative permissions are only required in order for Nerdio Manager to execute the domain join process automatically.
Azure Files joins the domain as a delegated service principal user object. In order to join the Azure Files storage account to the domain, the provided service account requires permissions on the target Organizational Unit (OU) that allows creating and writing new user objects. In addition, the service account also requires permission to set the Azure Files sign in account as delegated service. By default, this privilege is only provided to AD domain administrator users.
Delegate Permission to Create User Objects
The following procedure describes how to delegate permission to create and write user objects using Active Directory Users & Computers (ADUC, or dsa.msc).
To delegate permission to create user objects:
-
Locate the OU where Azure Files are to be joined.
-
Right-click the OU and select Delegate Control.
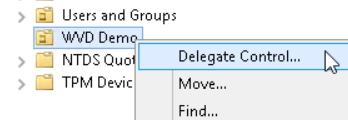
-
Add the Service User Account to be used for joining Azure Files to the domain.
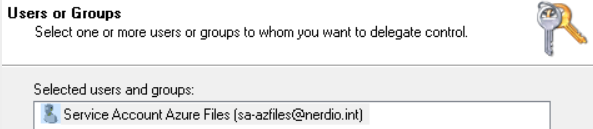
-
Delegate permissions to Create, delete, and manage user accounts.
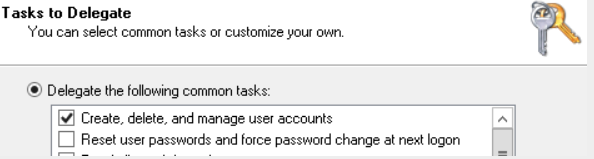
-
Select Finish to apply the changes.
Delegate Permission to Create Delegated Users
The following procedure describes how to allow the service user account used for joining Azure Files to the domain to mark the new object for Azure Files as a delegated service. This requires modifying the Default Domain Controllers group policy object in Group Policy Management (gpmc.msc).
To delete permission to create delegated users:
-
Right-click the Default Domain Controller's Policy and select Edit.
-
Navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > User Rights Assignment.
-
Locate the Enable computer and user accounts to be trusted for delegation policy.
-
Add to the policy the service user account name that is used to join Azure Files to the domain.
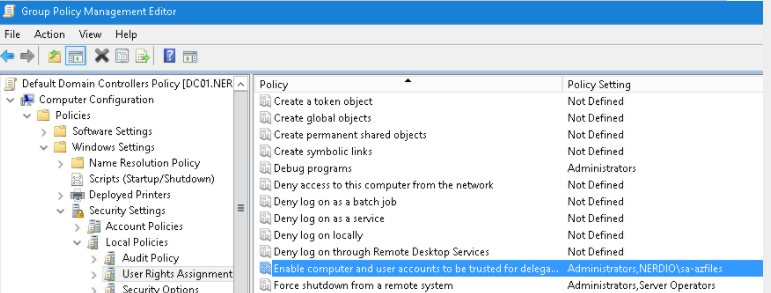
-
Close the editor.
-
Run gpupdate /force on all domain controllers.
Note: The policy change may take several minutes to apply after gpupdate completes.
Add Service Account in Nerdio Manager
You must provide the service account under AD Profiles in Nerdio Manager. See Entra ID join feature for details.